User verification and identity
Protect your platform from fraud and keep customer accounts secure with mobile identity signals and multi factor user authentication across sign-up, login and account management.
No credit card required Get started quickly Access all Twilio products

Use cases for OTP verifications and mobile intelligence signals
Implement a complete user verification solution to protect customers across the entire journey.
How to build secure user authentication
Implement a user authentication solution in days. No need to multisource vendors.
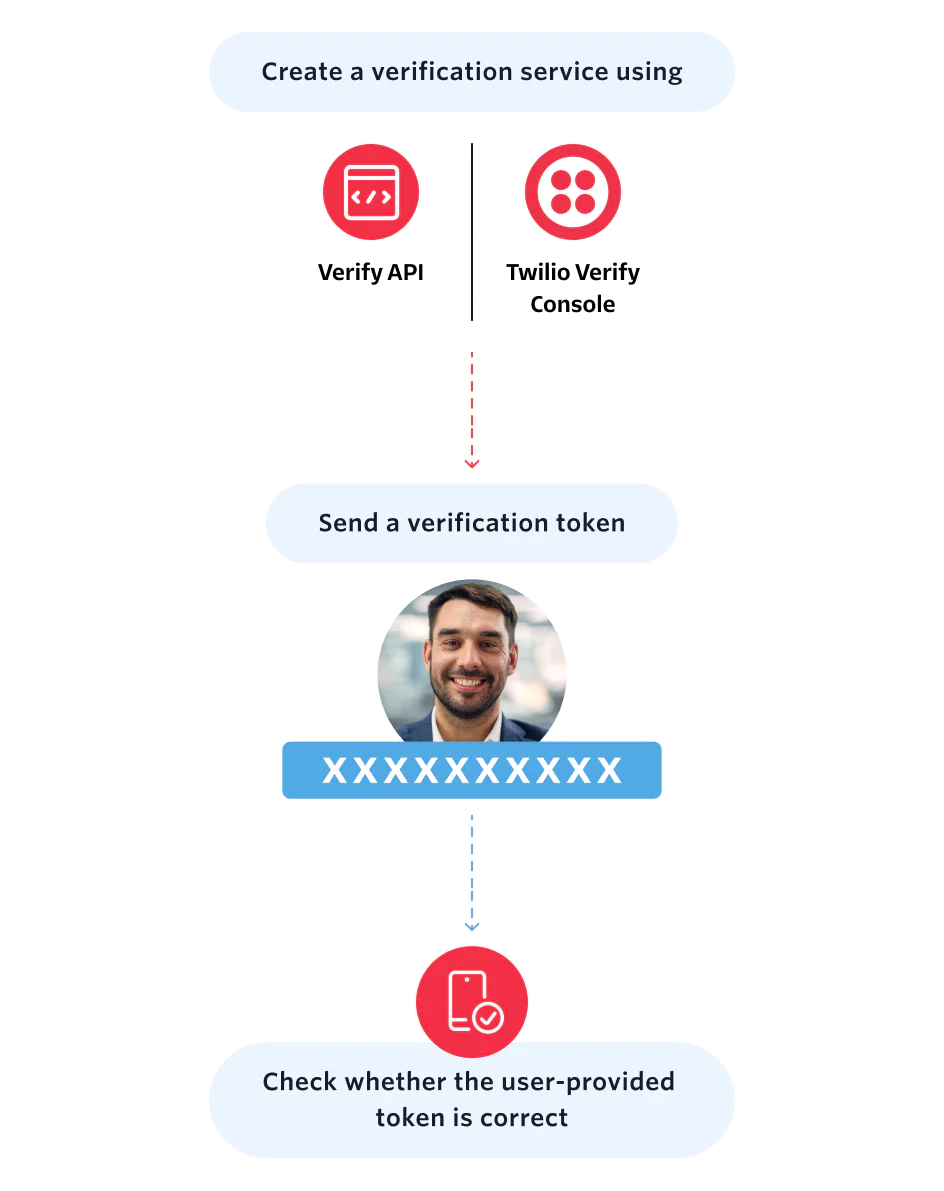
What you need to build intelligent user verification with Twilio
Easy-to-deploy APIs for user verification to prevent fraud, improve user conversion, and lower operational costs.
|
|
Verify |
Lookup |
|---|---|---|
|
What it does |
Turnkey API to verify users over any channel |
Query real-time phone intelligence data to verify phone number validity |
|
Channels |
SMS, RCS, WhatsApp, voice, email, TOTP, Push, Silent Network Authentication |
- |
|
Scale |
4.8 billion customer verifications per year |
Verify user identities across mobile, landline, fixed and non-fixed VoIP, toll free |
|
Reliability |
94%+ global delivery rate* Route optimization on Twilio Super Network for high deliverability |
Use mobile signals to confirm user identities reliably |
|
Conversion |
65%+ global conversion rate* |
Filter out unwanted or unreachable phone numbers with Line Type Intelligence and Reassigned Number |
|
Fraud prevention |
100% Protection from SMS pumping fraud with Verify Fraud Guard** Geo-permissions, rate limiting |
Identify potentially fraudulent numbers, SIM swapped numbers, numbers associated with SMS pumping |
|
Templates |
Carrier-approved templates that are automatically translated across 42 languages |
- |
|
Reporting |
Conversion and success rates per region, and channel |
- |
|
Learn more |
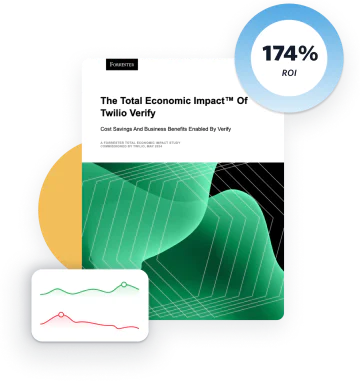

Forrester Consulting ROI calculator
A commissioned study by Forrester Consulting found Twilio Verify provided 174% ROI. Try our new calculator to estimate what your business can achieve with Verify.
Build and launch a verification use case in days
Sign up for a free Twilio account to start verifying user identities today. Use quickstarts, up-to-date docs, the Twilio CLI, and CodeExchange to build a prototype quickly.
Verify quickstart documentation
Get set up with a Twilio account, set up your development environment, validate phone numbers with Lookup, send your first phone verification token with Verify, and validate the token.
Lookup quickstart documentation
Get set up with a Twilio account, set up your development environment, validate phone numbers with Lookup, send your first phone verification token with Verify, and validate the token.
Why Verify over Programmable Messaging
Get set up with a Twilio account, set up your development environment, validate phone numbers with Lookup, send your first phone verification token with Verify, and validate the token.
Prefer not to code? No problem.
Work with one of our trusted partners to get coding support or explore a pre-built user authentication solution.


The Twilio difference
Fast and reliable delivery for user verification messages to keep your platform protected.

Verify Fraud Guard automatically blocks SMS pumping fraud. Geo-permissions prevent traffic in countries where you don't do business. And you also get protection against SIM swap and non-fixed VoIP (or fraudulent virtual numbers) with Lookup.
175+ million
fraud attempts blocked by Verify Fraud Guard
Twilio handles the complexities of carrier and government rules, so you can expand coverage quickly. Verify works in 200+ regions and translates messages automatically to match local languages.
42+ languages
translated within templates
Verify comes fully featured out-of-the-box, but it isn’t one-size-fits-all. You can choose your message template, delivery methods, and routing preferences—or write your own code.
4.5B+ verifications
through Verify annually
You only pay for each successful verification—vs paying per user, which makes it easy to scale up or down on demand.
$0.05 base price
for each successful verification
FAQs
Twilio Verify supports common authentication methods, including:
Two-Factor Authentication (2FA) / Multi-Factor Authentication (MFA): Verify uses OTP, TOTP, Push, or Silent Network Auth as a second factor to a password, or to combine multiple Verify factors.
Passwordless Authentication: Verify conducts passwordless authentication via Push approval, Silent Network Auth, or OTP-only login flows.
Token-Based Authentication: Verify delivers OTP (SMS/Voice/WhatsApp/Email) and TOTP, and Push uses asymmetric keys on a device.
Biometric Authentication: Verify conducts biometric authentication indirectly via device biometrics for approving Push (though there is no server-side biometric processing).
TL;DR: Twilio Verify specializes in possession-based factors (OTP, TOTP, Push, Silent Network Auth), it can optionally include on-device biometrics for Push, supports 2FA/MFA and passwordless flows, but does not provide knowledge, pure biometric, certificate-based, or location-based authentication as standalone offerings.
Twilio Verify supports passwordless authentication via possession-based factors like Push authentication, OTP (SMS, voice, WhatsApp, and email), TOTP, and Silent Network Authentication.
Twilio Verify will also have support for passkeys (WebAuthn/FIDO2) in Private Beta (coming September 2025). This will provide a managed WebAuthn backend so you don’t need a separate FIDO2 server. That means Verify can support phishing-resistant, passwordless authentication natively, alongside existing OTP, TOTP, Push, and Silent Network Authentication factors.
You can build and test a verification solution today with Verify. In this article, we show you how to send an SMS verification code in 5 minutes.
Twilio Verify is fully managed, so there is no need for lengthy hardware installation or maintenance, which significantly reduces implementation time.
The typical deployment time depends on the complexity of your use case. Simple use cases can be rolled out in days, whereas complex use cases may take a week to a few weeks to fully deploy.
Twilio provides MFA options including SMS, voice call verification, TOTP authenticator apps, and Push.
You can configure the Twilio platform to adjust authentication requirements based on risk signals. For example, you may set up controls to require additional verification for logins from new devices or locations. By applying adaptive, risk-based controls, you can provide additional security layers where they’re needed to reduce fraud, while reducing the hassle for users.
Yes. By design, Twilio’s products are built to help you meet regulatory requirements and security standards, like GDPR, HIPAA, and PCI DSS.
Twilio provides privacy and security controls, features like data minimization, user consent management, and secure data storage. Some products are HIPAA-eligible and customers can configure their Twilio usage according to HIPAA guidelines. The platform is PCI DSS compliant for handling payment card data.
Visit our Trust Center to learn more about Twilio’s privacy, security, and compliance.
Twilio’s cloud infrastructure is built for scale, supporting 5.1 billion validations annually across 180+ countries. The platform elastically adjusts to traffic spikes, ensuring reliable performance even during peak demand.
Twilio has global data centers and meets local compliance adherence so businesses can serve customers anywhere, without sacrificing speed or security.
If a user fails verification, Twilio Verify does not “approve” the attempt and your business should deny access or the action gated by verification. Twilio returns a non-approved/failed result. You control retries, lockouts, and fallbacks.
Twilio provides detailed dashboards, logs, and monitoring tools through the Console and APIs. Twilio customers can view metrics such as verification success rates, latency, geographic distribution, and potential fraud signals:
Verifications created, delivered, approved/denied/expired
Approval or conversion rate, average time-to-verify, retries per user
Breakdowns by channel, country, and carrier
Error code and failure reason distribution
Service-level filtering and time-range filtering
You also have the freedom to integrate with third-party tools and analytics platforms for advanced security monitoring to fine-tune your verification flows and maintain compliance.
Twilio Verify pieces are based on usage, with a list price of $0.05 per successful verification. You pay per verification or authentication event, plus any underlying channel and telecom costs (enterprise and committed-use discounts are available). The exact rates vary by country, channel, and volume.
Channel fees vary per channel:
SMS: Message attempts are always charged and not subject to delivery ($0.05 per successful verification + $0.0083 per SMS (US prices*)).
Voice: Voice attempts are always charged and not subject to delivery ($0.05 per successful verification).
Email: $0.05 per successful verification.
WhatsApp: Only billed when delivery is confirmed ($0.05 per successful verification + $0.0147 per authentication template message (US prices*)).
Passkeys: Pilot program.
Silent Network Auth: $0.05 per successful verification plus per-country channel fee. You will not be billed if we are unable to complete the SNA flow with the carrier.
TOTP (authenticator apps like Authy and Google Authenticator): TOTP channel fee is included in the verification fee. It’s charged when a request is approved.
Push and Silent Device Approval: Push channel fee is included in the verification fee. It’s charged when a request is approved or denied.
* You can find more detailed rates, international pricing, and links to channel-specific rates on the Verify pricing page.
* Based on those customers who provide conversion data
** Terms and conditions apply