-
 7 Ways To Secure Your AccountSecurity Brandon Sherman
7 Ways To Secure Your AccountSecurity Brandon Sherman -
 Is email based 2FA a good idea?Kelley Robinson
Is email based 2FA a good idea?Kelley Robinson -
 Is Someone Else Using Your Twilio Account? Best Practices to Protect Your Auth TokenShelley Wu
Is Someone Else Using Your Twilio Account? Best Practices to Protect Your Auth TokenShelley Wu -
 Twilio response to Voxox data breachTwilio
Twilio response to Voxox data breachTwilio -
 Evolving Our Trusted Bounty Program: Twilio Adds Safe Harbor to Bug BountyTwilio
Evolving Our Trusted Bounty Program: Twilio Adds Safe Harbor to Bug BountyTwilio -
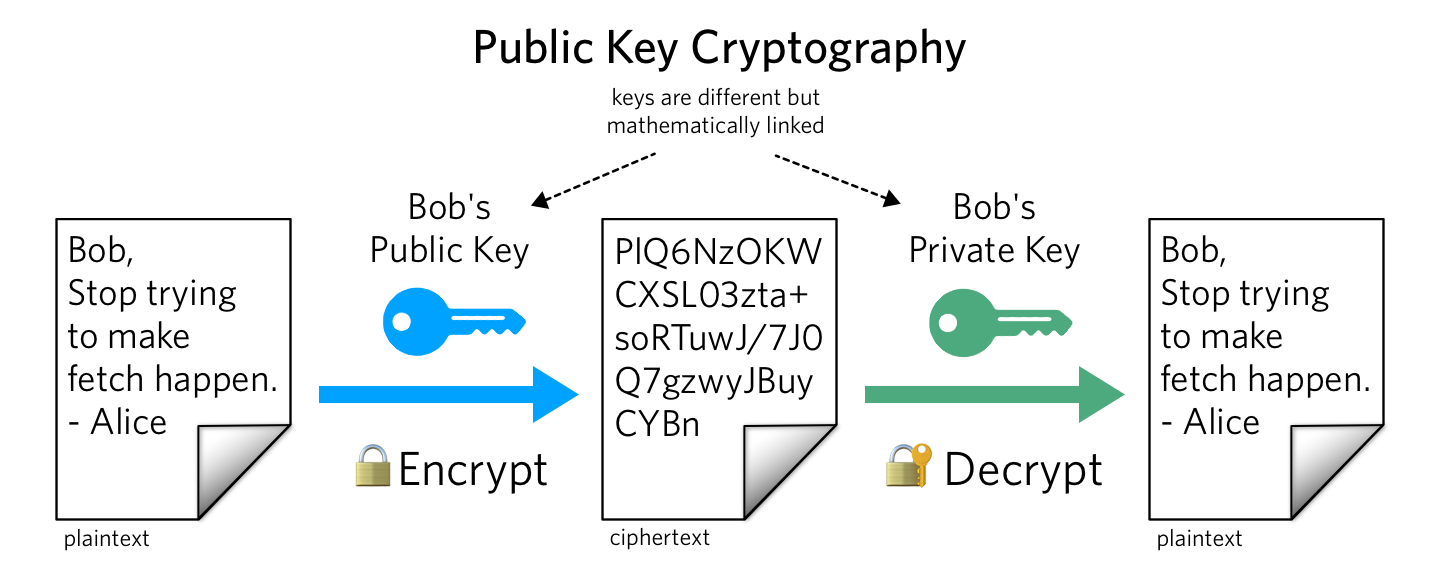 What is Public Key Cryptography?Kelley Robinson
What is Public Key Cryptography?Kelley Robinson -
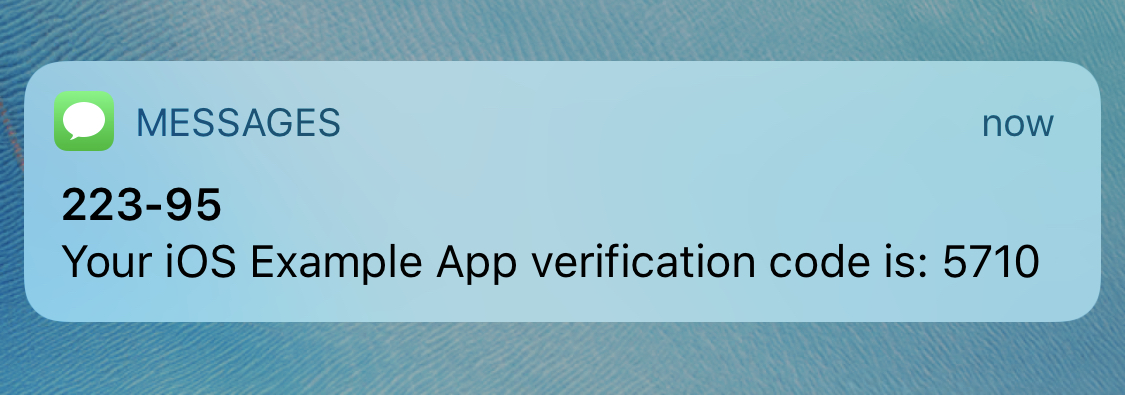 How to do Phone Verification in iOS Apps with Twilio Verify and SwiftKelley Robinson
How to do Phone Verification in iOS Apps with Twilio Verify and SwiftKelley Robinson -
 Getting Started with Apache Spark by Analyzing Pwned PasswordsKelley Robinson
Getting Started with Apache Spark by Analyzing Pwned PasswordsKelley Robinson -
 GDPR And EU Data Location RequirementsTom Tobin
GDPR And EU Data Location RequirementsTom Tobin