Understanding 2FA, the Authy App, and SMS
Time to read:
Understanding 2FA, the Authy App, and SMS
Authy was recently contacted by Decryptionary, a cryptocurrency and blockchain dictionary, with concerns about security vulnerabilities of using SMS for two-factor authentication (2FA) and questions about how SMS is used in conjunction with the Authy 2FA apps.
These are great questions. There has been an increase in phone porting attacks (sometimes known as SIM swapping). For those who aren’t familiar, a SIM card is a small, removable chip inside a mobile phone, carrying an identification number unique to the owner, and storing personal data. Phone porting is where cybercriminals trick your phone company into swapping your phone number to a different device and SIM card.
Typically, this is done when an attacker already has your username and password and also needs to get the two-factor authentication (2FA) text message as part of an account takeover. As such, the security industry and various media have been advising that users avoid using SMS for 2FA, and instead use apps on your phone (like our Authy app) which generate the same security code without the need for it to be sent via SMS.

The concern that Decryptionary has is if the Authy app uses SMS during the install process, isn’t Authy also vulnerable? This is another excellent question and one that we’ll be clarifying in this blog post.
Any 2FA security is better than none
First things first, SMS is not going away. The reason SMS for 2FA is so wildly popular is that it’s also incredibly easy to use. Since almost every online user has an SMS capable device these days, and practically the entire world is texting, there is no learning curve per se. And if a device is not SMS capable, two-factor authentication via a voice call covers almost everyone else.
While it is true that both these uses of the phone network are vulnerable to some form of attack, let’s remember one very important fact: two-factor authentication using SMS or voice is still far more secure than having no 2FA protection at all. But hijacking SMS is not as easy as other forms of attack. From a cybercriminal’s perspective, downloading a massive list of usernames and passwords, and then automating account takeovers, is fairly simple. But convincing multiple wireless providers to make changes to hundreds or thousands of customers phone plans takes a lot more effort and is much harder. So yes, using SMS is not without risk, but it’s riskier to use nothing.
Avoid security risks with a mobile 2FA app
If you have a smartphone or other mobile device, you can avoid using SMS and voice calls to get your 2FA code by downloading and installing one of many popular two-factor authentication apps directly to your device. This is a much more secure method for your 2FA login. Apps like Authy or Google Authenticator generate something called a Time-based One-Time Passcode (TOTP) directly within the app. So even if an attacker tricked your cell service provider into completing a SIM swap, they still wouldn’t have access to your authentication codes. The data needed to generate those codes remains on your physical device, not within the SIM card.
At this point, you may be asking yourself “Doesn’t the Authy app use SMS as part of the app installation?” The answer is yes, and the reason is that we use your phone number as your identity, instead of something like a username and password. The first time you install Authy, we need to verify you and ensure that you have access to the phone number you claim to own. Also, typically, the first time you download Authy, you’re not yet protecting any accounts with Authy 2FA, so security concerns over SMS at this step are low risk.
Additional considerations to make your use of the Authy 2FA app even more secure
1 – Set a backup password
Now that you’ve got Authy installed on your phone, you’ll want to set up your first 2FA accounts. You accomplish this by using the app to scan a QR Code (provided by the site on which you’re looking to protect an account). Once you capture your first code and protect your first account, you’ll likely start securing other accounts.
At this stage you have an important decision to make: do you keep all of your 2FA tokens on a single device, or back them up to the cloud? If you chose to the single device option — and you either lose the device, upgrade it, or have it stolen — you’ll need to convince every service where you’ve enabled 2FA on to switch it off. Then, when you replace your phone, you’ll need to get back into your account so you can manually re-enable 2FA on each service once again. The typical user can’t appreciate how painful this exercise is until it actually happens. Just ask anyone who lost access to their Google Authenticator accounts. It’s a nightmare.

This is why Authy allows you to backup your 2FA tokens to our secure cloud storage – accessible to only you so that you can always reinstate your accounts when you replace a lost, stolen or out-dated device. When you backup 2FA tokens to the cloud, we ask you to set a backup password, and we use this password to encrypt your data and then sync it to our cloud service. Since we never physically store your password, your data is exceptionally secured in our cloud platform — BUT — it’s super important that you remember this password. It’s something only you will know.
2 – Install Authy more than once
Next, we highly recommend installing Authy on another device. If you’ve synced your tokens to the Authy cloud, we will automatically sync them to each device you have Authy installed on. (Note: if you only have one mobile device, you might want to also download our browser-agnostic Authy Desktop app).
When you attempt to install another instance of Authy, a new method of verification is available via the first (or any other) Authy app you’ve installed. This is a significantly more secure method of verification, because we check the new device against an existing device we already trust. SMS is still an option at this point, and this is where the vulnerability of SMS once again causes a problem, but there is a simple way to protect yourself further.
3 – Turn off Authy’s multi-device feature
Now that you have two (or more) Authy apps installed on separate devices. We highly recommend opening the Authy app, going into Settings, and switching off the multi-device option (see below).
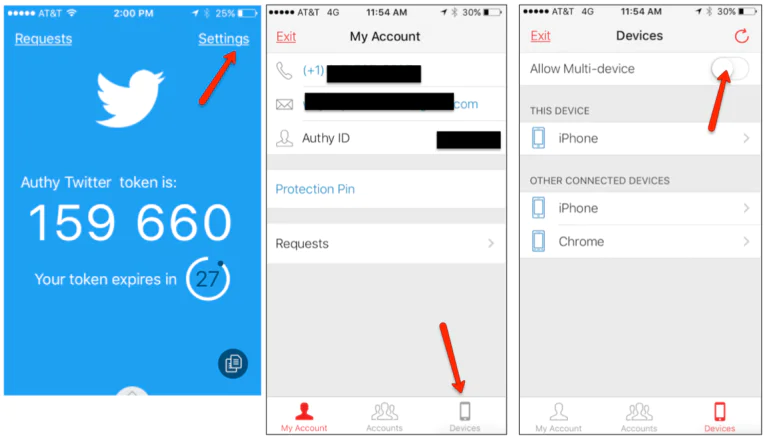

What this means is that no additional apps can be installed. All the Authy apps on your existing devices will continue to work as designed and with no interruption, but no new apps will be able to be downloaded to new devices moving forward. So, even if anyone has been able to get your username and password, or SIM-swapped your phone number, there is still no way they will be able to access your 2FA data synced with the Authy service. If you ever need to install Authy on a new device, simply re-enable multi-device, install Authy, and then disable the setting again.
Why isn’t the multi-device setting turned off by default? It’s a case of balancing security versus usability. We decided to keep the multi-device feature set to the “on” position after confirming that the number of people who lose a device, are unable to re-install Authy, and are permanently locked out of their online accounts is much higher than the number of SMS-based account takeovers. And we’re using this blog and other tools to convey the importance of downloading additional instances of Authy and then deactivating the multi-device feature. While the vulnerabilities of SMS and voice are real, the user experience must also be a consideration.
4 – Some limitations if you are high-risk
You might find that when installing a second Authy app, you may not have SMS or voice available as an option. Instead, you are directed to use an existing Authy app or presented with the opportunity to recover your account. This is because we automatically switch off the ability to use SMS to install more Authy apps if we identify your account is high-risk. If you no longer have access to your other Authy apps, and this is preventing you from installing a new one, you will need to go through our recovery process. Admittedly, this isn’t an ideal user situation, but it’s better than having your Twitter handle taken over by a hacker or losing all your bitcoin.
5 – 2FA Recovery
Imagine this scenario: You installed Authy, lost your phone, your laptop is broken, and the bitcoin price is climbing like crazy. You need to login to your crypto wallets, but you either enabled multi-device and all the devices with Authy are not working or accessible, and your account has been tagged high-risk, and you can’t use SMS to install a new Authy app. What are your options?
Authy has a 24-hour account recovery process. By providing your phone number to Authy Support, we can go through a set of security processes to re-enable your ability to install Authy. Some users may question why account recovery isn’t instantaneous, but our goal is to 100% protect our user’s accounts against an attack or hack, and that includes our recovery process. This 24-hour period allows us the time to perform the necessary due-diligence to verify that you are who you say you are. We’d be doing a disservice to all if we were to rush this process.
Even better protection when the Authy app is combined with the Twilio 2FA API
The Authy apps actually have a companion API which Twilio sells to application developers. This API negates for the need to scan a QR code, instead 2FA tokens are sent directly to the apps. Some sites you use (for example Twitch, Pinterest, SendGrid, CloudFlare, Gemini, Uphold and more) might use the Authy API and they chose so because developing a 2FA solution for your own applications can be complex and risky. Also when using the API, it’s possible to leverage even more security to defend against the threat of SMS vulnerabilities.
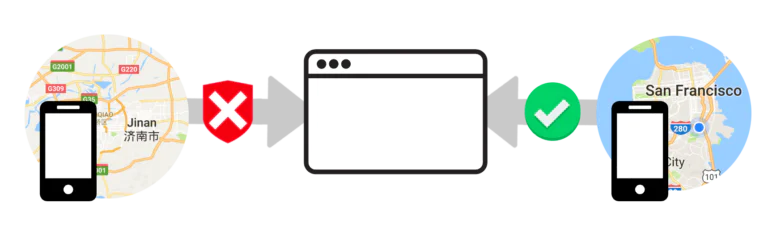

While not apparent to the user, the Twilio API is embedded into an application’s code and can identify where a 2FA token is requested from and how the device requesting it was registered. By arming the authentication with device data, the owner of a website or app can make better decisions concerning user protection. This could include security options like:
- Prohibiting SMS-based 2FA for high-risk users or transactions.
- Assessing risk based on location by comparing the IP address and region of the initial Authy app registration with the IP and region currently being used for authentication.
- Blocking 2FA codes from Authy for Desktop apps when users attempt access to a site’s web interface, thereby forcing 2FA by mobile device. (Or, when a user is accessing a mobile application only allowing 2FA codes from the Authy desktop app).
If you want to understand more about the Authy API and how it can help make 2FA even more secure, read about the device data available or look at the product information over on www.twilio.com/authy.
So, where are you using Authy 2FA?
Authy is committed to helping customers of more and more banks, gaming sites, email providers, and other businesses stay secure. Our reliable two-factor authentication tokens are as simple to use as any other smartphone app and won’t slow you down at all. Whether it’s securely shopping online, transferring money, or communicating through a favorite social app, Authy is found in more places than ever.
In fact, we can help you be protected on more sites than you’re probably even aware of. Many sites offering 2FA suggest that their users protect themselves with Google Authenticator. If you run across those, know that you can use Authy wherever Google Authenticator is recommended!
Just remember to backup your Authy account to the cloud, install Authy on at least one additional device, and then turn off our multi-device feature.
We’re sure you’ll agree that there’s no better — or easier to use — two-factor authentication app out there.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.

