Secure FreeRADIUS VPN Users With Twilio 2FA
Time to read:
This post is part of Twilio’s archive and may contain outdated information. We’re always building something new, so be sure to check out our latest posts for the most up-to-date insights.

FreeRADIUS is the most widely deployed RADIUS server in the world, supplying many Fortune 500 companies and Tier 1 ISPs with the means for world class authentication. With more than 50,000 sites and over 100 million people using FreeRadius to access the internet, that’s a lot of authenticating.
Twilio has recently developed a solution which extends the FreeRADIUS tooling to request a second-factor when authenticating via push-notification or a TOTP (time-based one-time password) token generated on a user’s phone. This solution works with both OpenVPN and Cisco AnyConnect VPN.
Choose your 2FA Flavor
We designed the Twilio / FreeRADIUS integration to work in one of four ways. Our TOTP solution works with Authy SoftToken, our most popular, user facing 2FA app. If you choose to offer a push-notification technology, you’ll be working with our Authy OneTouch product. Below you’ll find outlines and flow diagrams of these approaches. And you can find the FreeRADIUS module on the Authy Github as well as the Installation Guide PDF and Release Notes PDF.
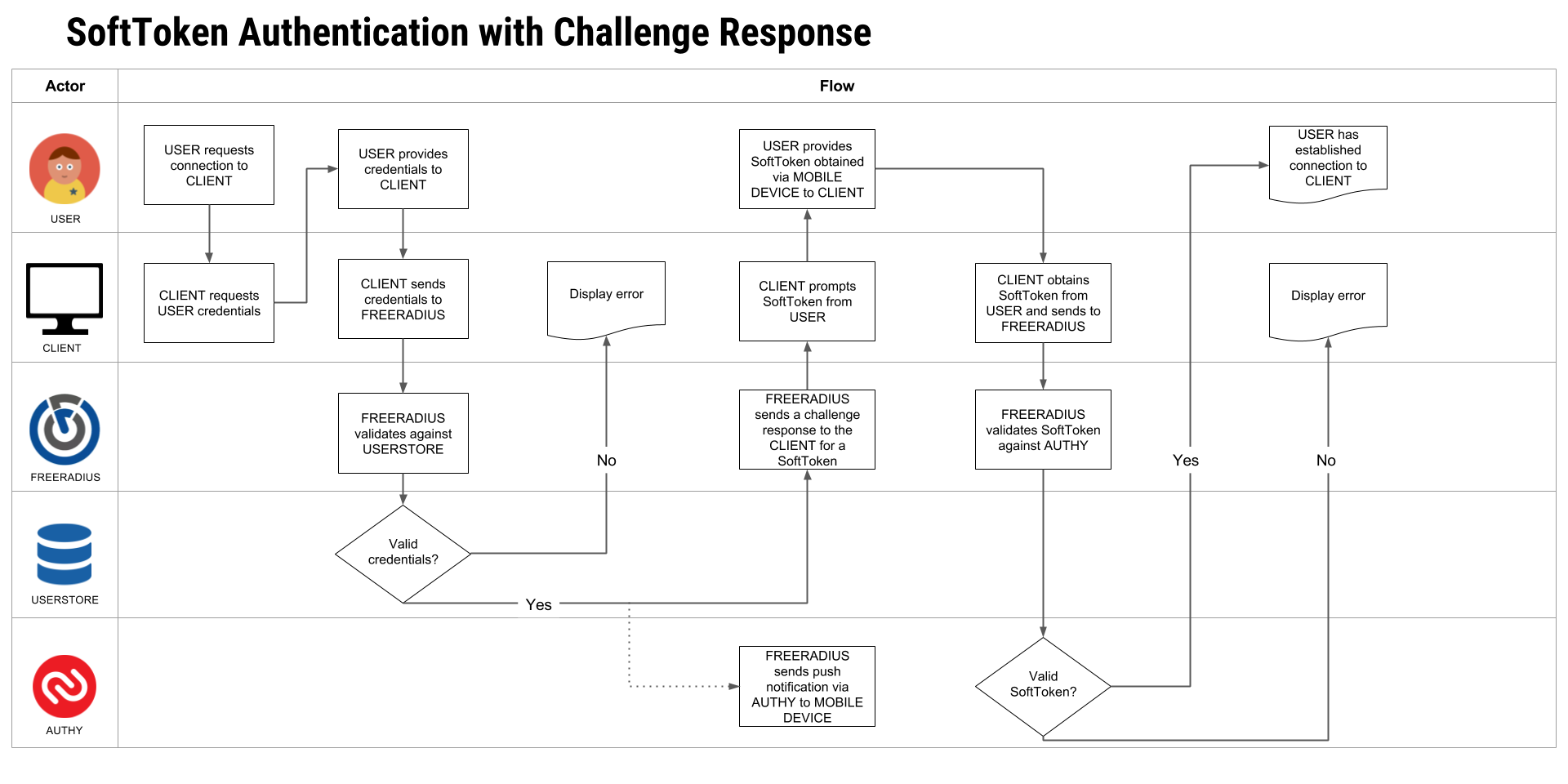
SoftToken Authentication with Challenge Response
In this scenario, once a user has entered their username/password credentials, FreeRADIUS prompts for SoftToken authentication via the Authy app. The FreeRADIUS installation then validates the SoftToken against the Twilio 2FA service. If validation is successful, FreeRADIUS grants access to the user.
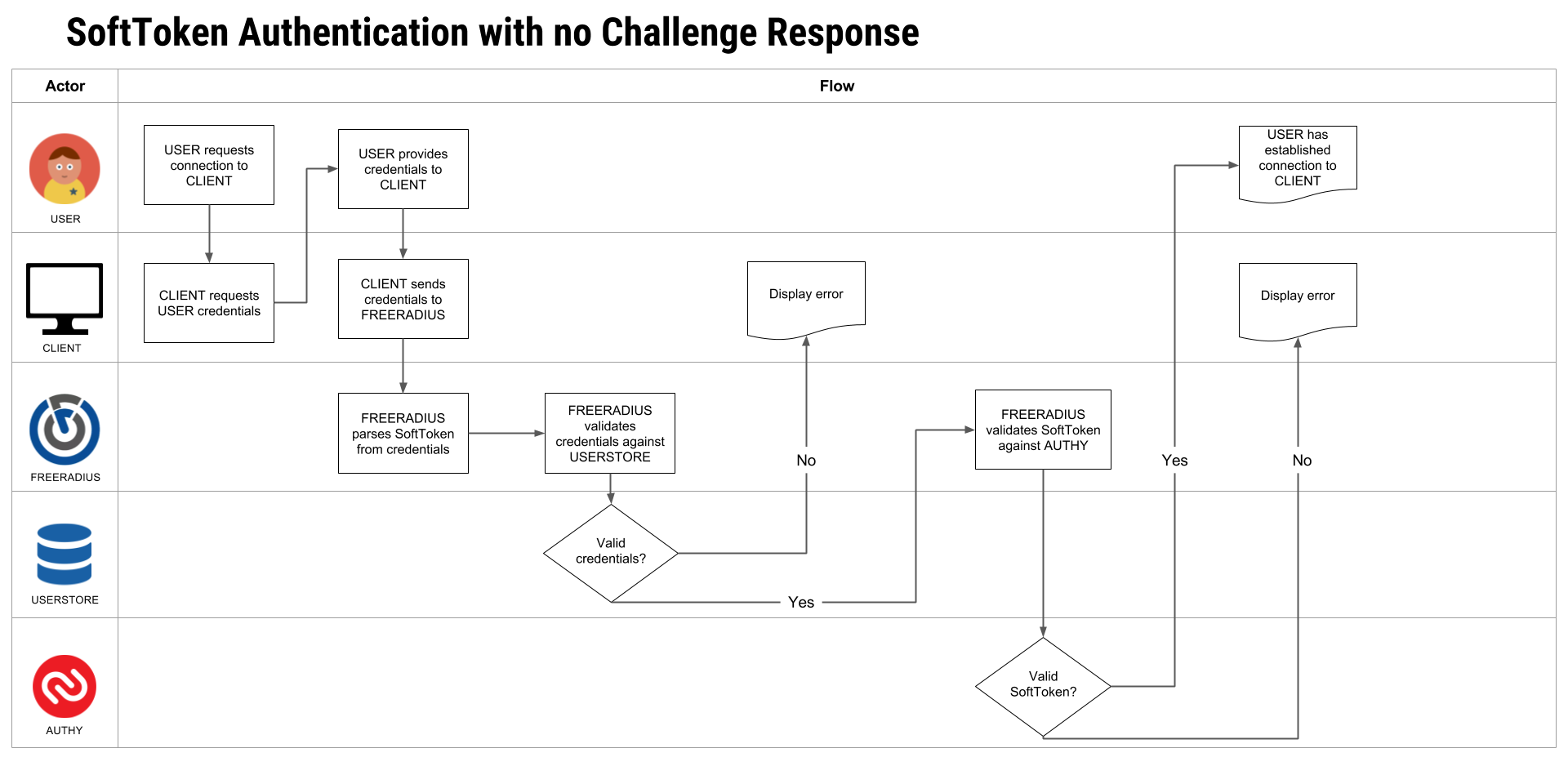
SoftToken Authentication with No Challenge Response
In this scenario, the user appends the SoftToken to their username/password credentialing during authentication — a common approach among VPN vendors. Generally, there is a predefined delimiter character which separates the password from the TOTP token and is easily modified inside the FreeRADIUS module’s configuration. Let’s look at that flow:
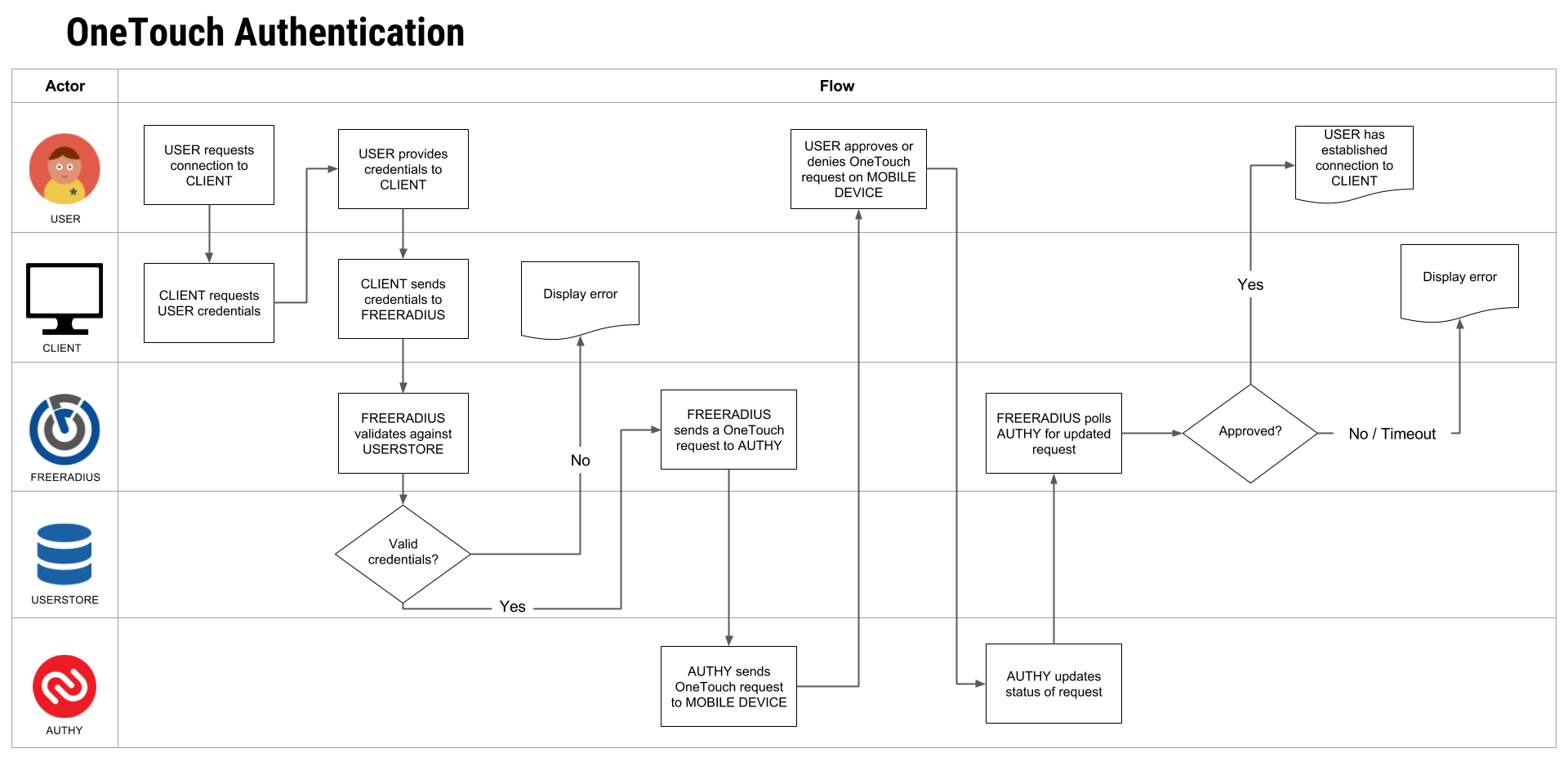
OneTouch Authentication
In addition to TOTP, you can also use push notification to prompt users to ‘Approve or Deny’ VPN access. Setting up Twilio’s OneTouch authentication is a little more involved as you’ll need to setup an endpoint to either poll the Authy API checking for a OneTouch status change or process a OneTouch callback. You can find this Authy Callback code and configuration on our Github repo as well.
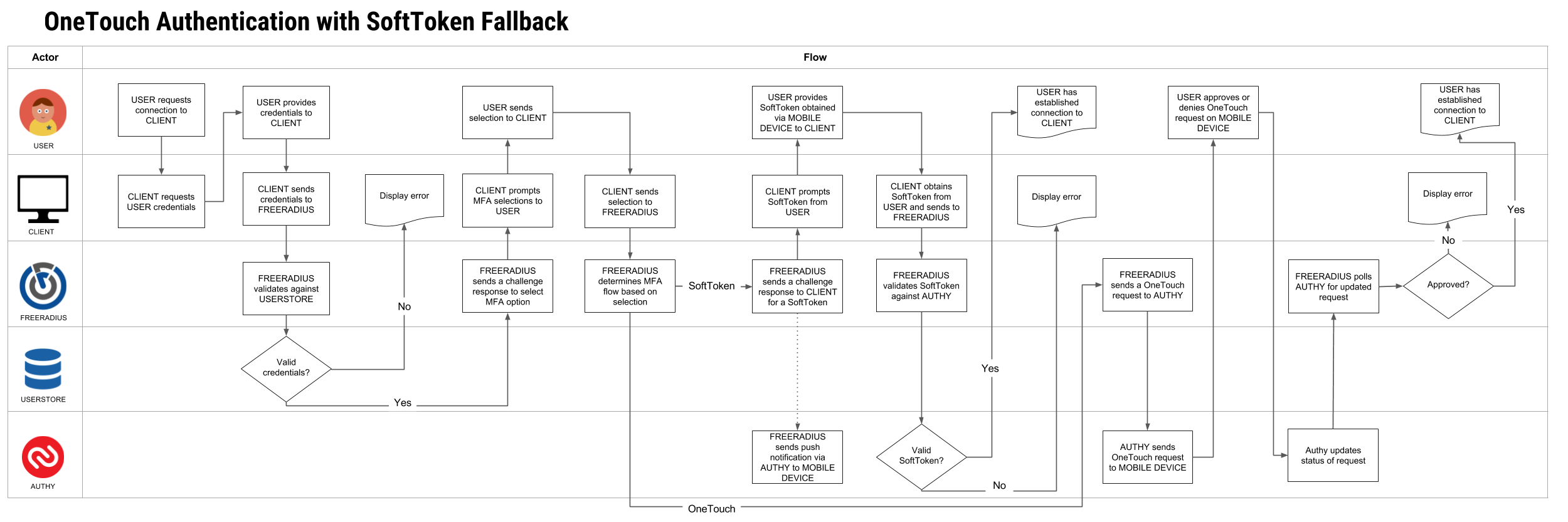
OneTouch Authentication with SoftToken Fallback
Lastly, you might also prefer to employ push-notification 2FA with a fallback to TOTP delivery. After entering username/password credentials, the user will be prompted to choose to authenticate via OneTouch or SoftToken. Here’s how that might flow:
VPN Users Secured
If you’ve read this far, you’re probably thinking about setting up a FreeRADIUS install. As you can see, Twilio’s FreeRADIUS solution provides a number of workflows to authenticate users allowing you to choose the best approach based upon your planned user experience. When considering your approach, keep in mind that the workflows shown above, and the user messaging, are entirely configurable.
Feel free to reach out to us about your experience. Write to us at sales@authy.com with comments or suggestions.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.