How to Secure Your SIP Trunks with Twilio
Time to read:

The world has changed, thanks to the Internet. We are able to collaborate and build quickly and efficiently. But – this phenomenon has also increased the number of security risks and attempts by hackers to extract valuable information.
Here at Twilio we use Rest APIs which are secure by default. On top of that, our Elastic SIP Trunks can be secured by simply flipping a switch.
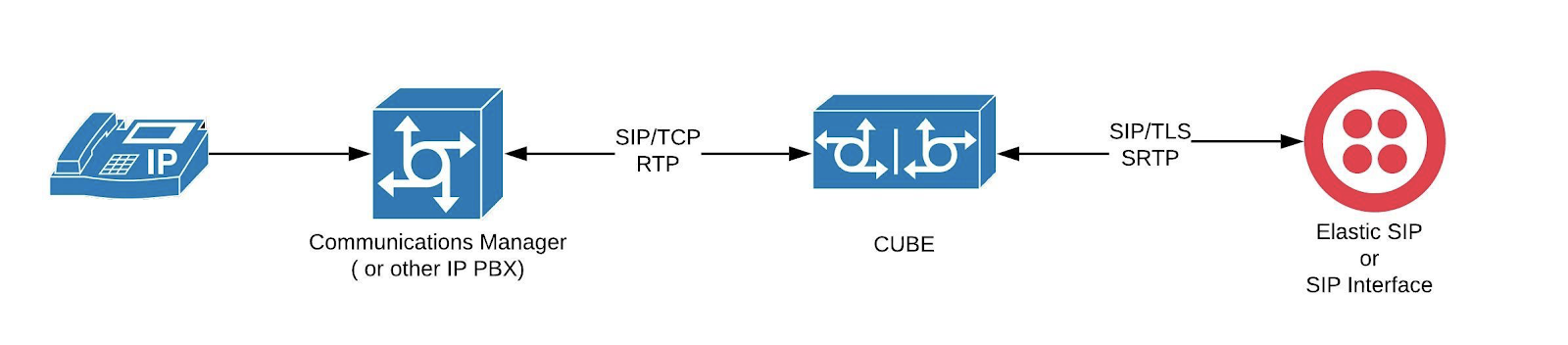
If you have not turned on the secure feature for Elastic SIP Trunk, this post will give you the reasons you should do it. We’ll show you how to enable Secure Trunking and walk through configuring a Cisco Unified Border Element (CUBE) with TLS & SRTP.
TLS/SRTP is now included 🎉
We are now offering this security feature free – all you need to do is flip the switch! Learn about the TLS specification for secure SIP trunking in our docs.
We have already documented the steps needed to configure Twilio with several popular vendors. (You can find them here.) The latest addition is the Cisco Unified Border Element (CUBE).
This blog post will walk you through the following:
- How to enable Secure Trunking on the Twilio Trunks
- How to configure a Cisco Unified Border Element (CUBE) with TLS & SRTP
- How to troubleshoot various failure scenarios
Enable Secure SIP trunking and configure a Cisco CUBE
In the following steps, we'll first walk through securing your Elastic SIP trunk with Twilio. Once that is ready, I'll show you how you would configure a Cisco CUBE to take advantage of the setup.
Let's get started.
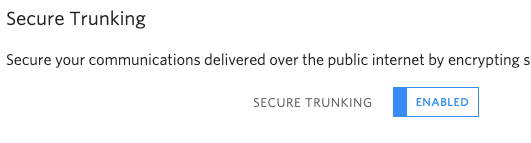
Step 1 - Enable Securing Trunking
From the Twilio console, navigate to the Elastic SIP trunk and toggle secure running to ENABLED
Step 2 - CUBE Configuration
1. First, generate an RSA key on the CUBE by running these instructions from the command prompt:
crypto key generate rsa modulus 2048 general-keys label RSA2048
2. Next, create a PKI trustpoint:
crypto pki trustpoint cube1
enrollment selfsigned
revocation-check none
rsakeypair RSA2048 20483. Generate the certificate with the following command:
crypto pki enroll cube1
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Generate Self Signed Router Certificate? [yes/no]: yes4. Import the Digicert global root CA certificate
crypto pki trustpoint twilio
enrollment terminal
revocation-check none
rsakeypair RSA2048 2048
crypto pki authenticate twilioYou will be prompted to paste the Digicert Global CA pem text into the terminal. This text can be found here
% Do you accept this certificate? [yes/no]: yes
crypto pki enroll twilio
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Display Certificate Request to terminal? [yes/no]: no5. Set the SRTP auth cipher.
voice service voip
sip
srtp-auth sha1-806. Create a dspfarm profile to support SRTP-RTP interworking.
dspfarm profile 1 transcode universal security
codec g711ulaw
maximum sessions 12
associate application CUBE7. Update the sip-ua settings
sip-ua
transport tcp tls v1.2
crypto signaling default trustpoint cube18. Finally, enable STRP & TLS on the dial-peers facing Twilio.
dial-peer voice 205 voip
srtp
session transport tcp tls
Good job! If everything went as planned, you should now have a secure SIP trunk up and running.
Troubleshooting common issues with TLS & SRTP
There are a lot of things that can go wrong when enabling TLS & SRTP. To help in troubleshooting I’ve outlined some errors I ran into and helpful debug commands that can be used to get to the bottom of it.
Symptom-1 - Call immediately fails
Debug command: debug ccsip messages
SIP/2.0 488 Secure SIP transport required
If tls isn’t enabled on the dial-peer the call will immediately be rejected with the above message.
Symptom-2 - Calls towards CUBE generate a fast busy
Debug command: debug crypto pki validation
Jun 24 15:36:17.315: CRYPTO_PKI: (A00A5) No suitable trustpoints found
Validate that the Digicert Root CA has been added to the router.
Symptom-3 - Calls from PBX to PSTN return a fast busy as soon as the call is answered
Debug command: debug ccsip messages
a=crypto:1 AES_CM_128_HMAC_SHA1_80 inline:zcCGar0v7JnoVEaAvVGmH/BYw1LY05GET2YaElNp
If SRTP is enabled globally under: voice service voip and CUCM is not running in a secure mode, CUBE will attempt to negotiate SRTP and the call will fail. Issue the following command to disable SRTP globally.
voice service voip
no srtpSymptom-4 - Calls from PBX to PSTN return a fast busy after a couple rings
Debug command: debug ccsip messages
SIP/2.0 503 Service Unavailable
Confirm the dspfarm is configured and active. If SRTP-RTP interworking is required and the dspfarm isn’t active, the call setup will fail.
BDM-border#show dspfarm profile 1
Dspfarm Profile Configuration
Profile Admin State : DOWN
Profile Operation State : DOWN
Application : CUBE Status : NOT ASSOCIATED
If the Profile Admin State AND Operation state are “DOWN” issue the following command. The Admin State should be “UP” and the Operation State should be “ACTIVE”
dspfarm profile 1
no shut
BDM-border#show dspfarm profile 1
Dspfarm Profile Configuration
Profile Admin State : UP
Profile Operation State : ACTIVE
Symptom-5 - Calls towards the PBX fail and debug ccsip messages doesn't return anything
Debug command: debug ssl openssl errors
BDM-border#debug ssl openssl errors
TLS errors debugging is on
BDM-border#
.Jun 24 16:31:04.901: opssl_SetPKIInfo entry
.Jun 24 16:31:04.901: CRYPTO_OPSSL: Can't find router cert.This happens when the cube trustpoint is not valid. The following command can be run from a *nix system to confirm that CUBE is returning a certificate.
openssl s_client -host 192.168.210.190(replace with cube ip) -port 5061 -prexit -showcerts
When the certificate is not valid the following will be returned:
See the example certificate in GitHub
4526089836:error:140040E5:SSL routines:CONNECT_CR_SRVR_HELLO:ssl handshake failure:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22.260.1/libressl-2.6/ssl/ssl_pkt.c:585:
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 0 bytes
---With a valid certificate the following will be returned:openssl s_client -host 192.168.210.190 -port 5061 -prexit -showcerts
See the example certificate in GitHub
CONNECTED(00000003)
depth=0 CN = BDM-border
verify error:num=18:self signed certificateCongratulations! You’ve learned how to configure secure SIP trunking on a Cisco CUBE. If you want to learn more, the following resources may be useful to you
Resources:
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


