Configuring SSO with any other SAML2.0 Identity Provider
Twilio Editions feature
Single Sign-On is available to all Twilio Editions customers. Learn more about Editions.
This guide covers configuring your SAML 2.0 Identity Provider with Twilio for SSO login to Twilio Console. If you are looking to Configure SSO for Twilio Flex or SendGrid, refer to the configuration guides for them:
Before proceeding with SSO Configuration make sure that you have satisfied all of the prerequisites.
Go to Admin Center and click on the Single Sign-On option in the navigation bar as shown below
Create a new SSO Profile by clicking the 'Create new SSO Profile ' button. You will land on the below screen where you can copy or download the SP Metadata.
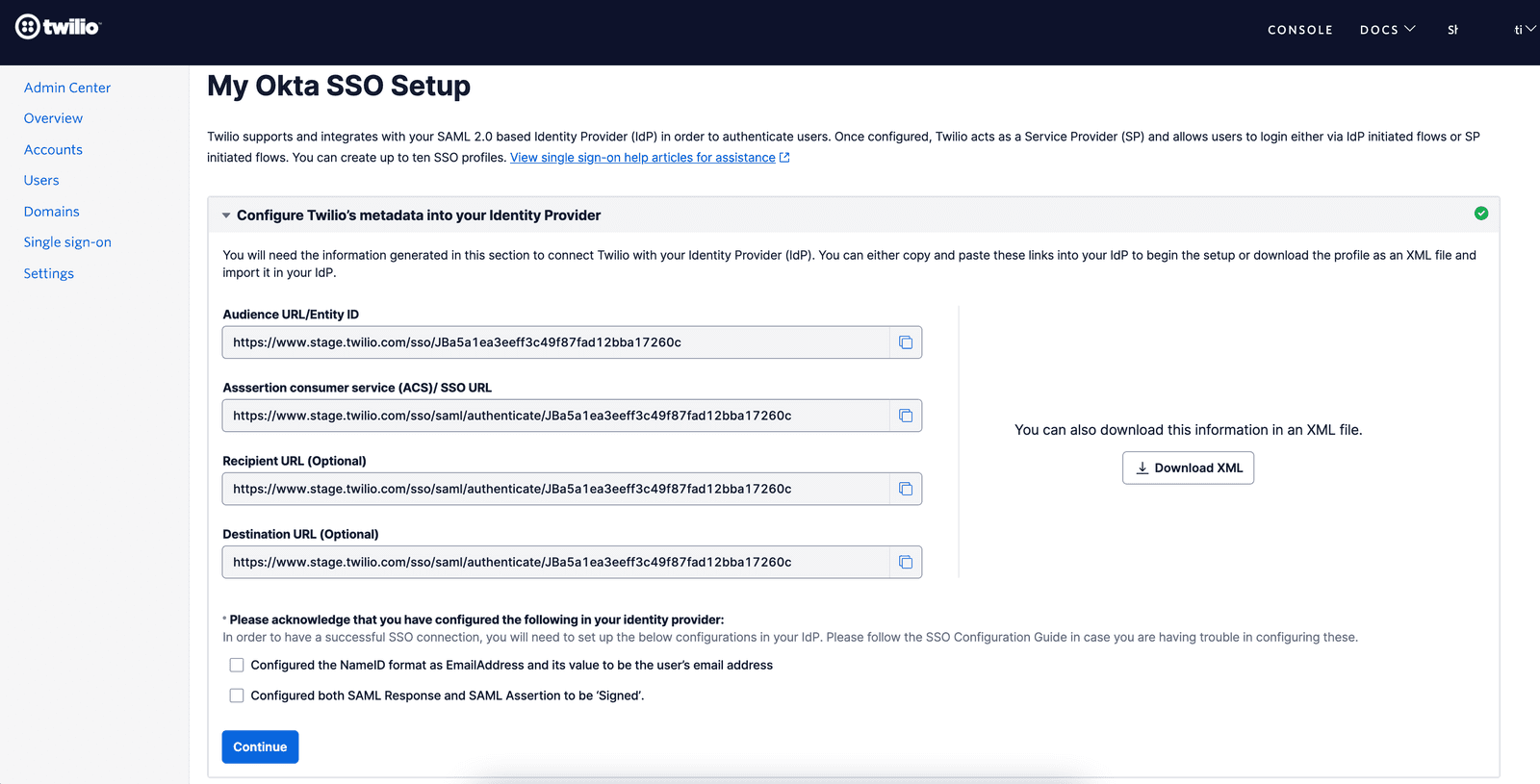
Keep this tab open as you will need these values to configure a SAML application in your IdP
You will need to create an application or integration that will enable your users to be able to log in to the Twilio Console via SAML single sign-on.
If your IdP supports multiple login methods for the application then please make sure to select SAML 2.0 as the login method.
Provide an appropriate name to the Application and if your IdP supports then upload Twilio Logo so that your users can recognize and use the application.
For your IdP to recognize Twilio SSO you will need to copy and paste the following values from the Twilio SSO Profile you created in Step 1 -
- Audience URI/Entity ID: this value will be used by your IdP to specify the entity or audience the SAML Assertion is intended for
- Assertion Consumer Service (ACS) URL or Single sign-on (SSO) URL: This is the Twilio URL where your IdP should send the SAML Response
- Recipient and Destination URLs: If your IdP requires these values to be configured separately then populate the same value as ACS/SSO URL in these fields as well
- Default Relay State: should be left blank
Apart from the above, you'll also need to configure NameID and Signing Option settings in your IdP -
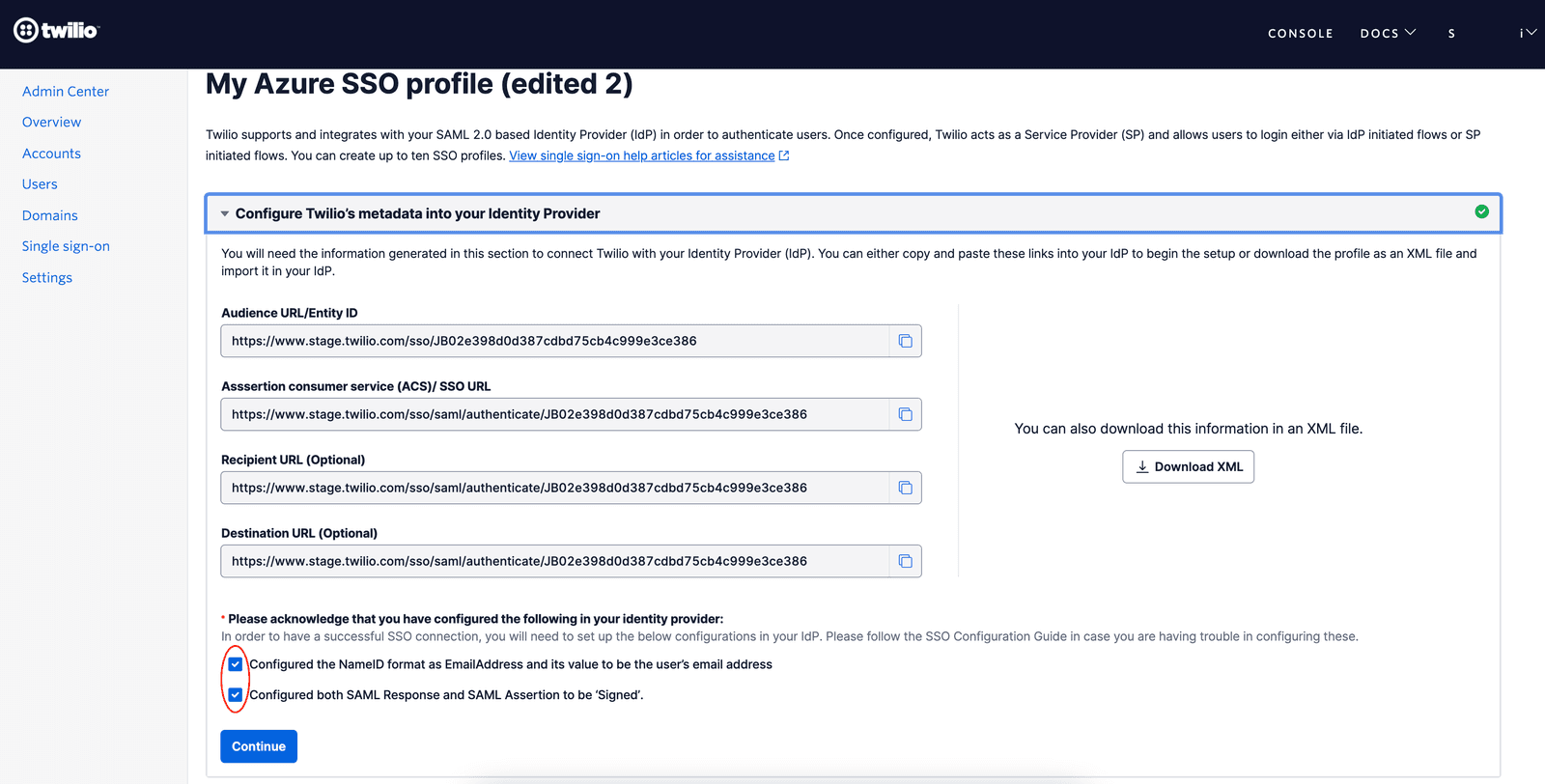
- NameID: The NameID format should be EmailAddress and its value should be configured to the email address attribute of your users.
- Signing Option: You should configure your IdP to send 'Signed' SAML Response as well as 'Signed' SAML Assertion to Twilio.
- Encryption: Twilio SSO does not support encrypted SAML response. So make sure that your IdP is configured to send unencrypted SAML responses.
Go to the tab where you have the Twilio SSO Profile opened. Confirm that you have configured the Signing Option and NameID settings in your IdP and click on Continue
In the next step, please update the friendly name of the SSO Profile to an appropriate value that you can recognize.
Then select the Identity Provider from the dropdown. If your Identity Provider is not there in the dropdown then select 'Other/Generic SAML 2.0'
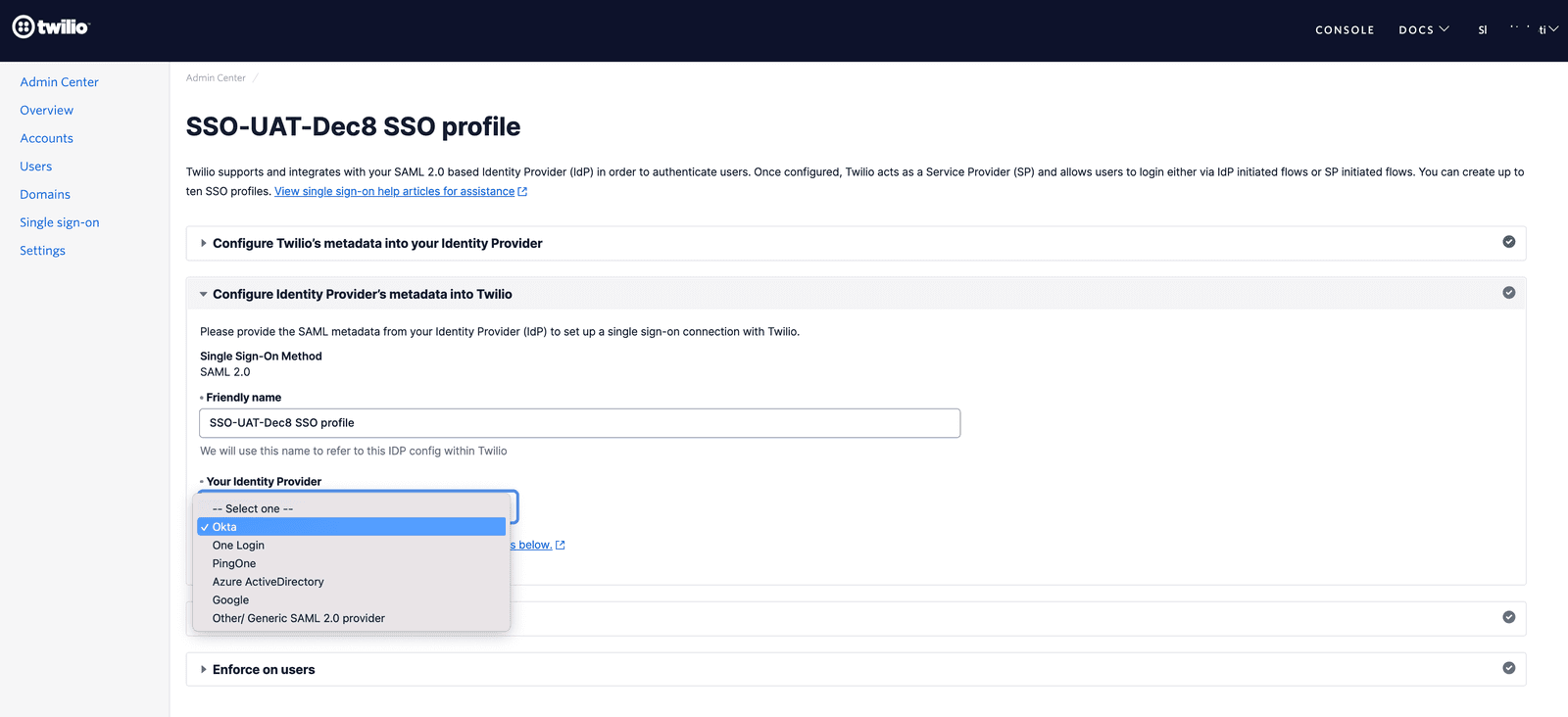
Upon selecting the Identity Provider you will see the IdP metadata fields as shown below.
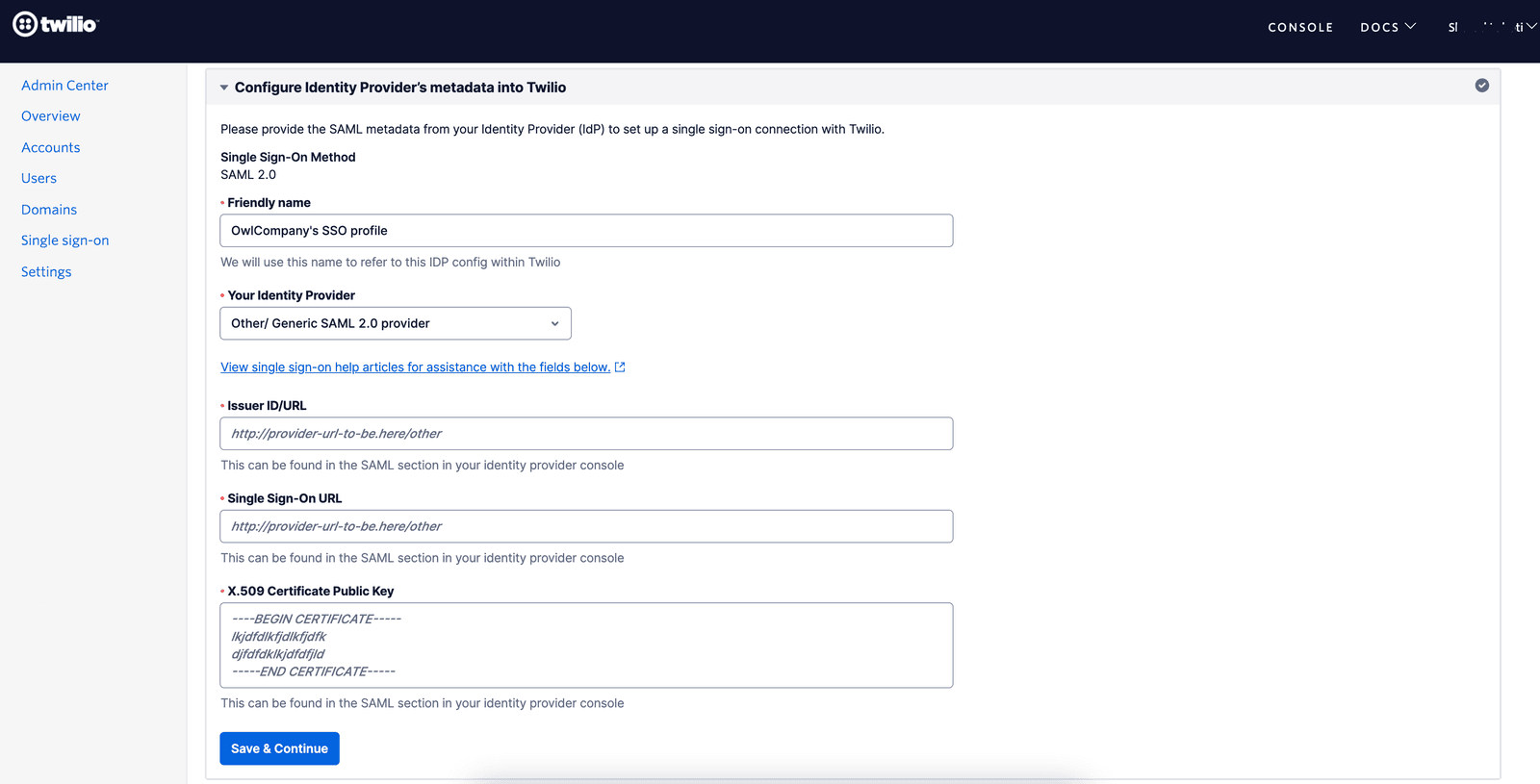
You will need to copy and paste the following values from your SAML Application in your Identity Provider -
- Issuer ID/URL: This is also known as 'Identity Provider Issuer', 'Issuer' or 'Identifier' in some IdPs. This issuer value will be sent by the IdP in SAML assertion and Twilio will verify that the value configured here matches the value present in the SAML assertion.
- Single sign-on URL: This is also known as 'SAML Endpoint', 'Login URL' or 'IdP SSO URL'. This is the URL where Twilio will send the SAML requests for authenticating users in the SP-initiated login flow
- X.509 Signing Certificate (Public Key): This should be the public key of the certificate that will be used to sign the SAML Response and Assertions for the SAML application you have configured in your IdP.
Once you have configured the 3 values, you can click on 'Save & Continue' to save the configured SSO profile and proceed to the next step to test the SSO connection.